
Use MS-101 dumps PDF and MS-101 dumps VCE from leads4pass MS-101 dumps: https://www.leads4pass.com/ms-101.html (total questions: 432 Q&A). All exam questions and answers have been verified by the Microsoft professional team to ensure 100% passing of the Microsoft 365 Mobility and Security certification exam.
We update our Microsoft MS-101 dumps exam questions and answers once or twice a month!
All questions and answers have been verified by a professional team to ensure authenticity and effectiveness.
We update free 365 days based on effective feedback and absolutely guarantee timely and effective questions and answers. So you are in luck! Every update you get here is immediate. For more Microsoft Exempt Certification Exam Practice Questions, visit: Fulldumps.com
Share some free Microsoft MS-101 dumps PDF downloads online:
https://drive.google.com/file/d/18kdzNZGRvo-KFvGCwf6uKlrToedMOnJU/
Read some Microsoft MS-101 Dumps exam questions and answers online from leads4pass
| Number of exam questions | Exam name | From | Release time | Last updated |
| 15 | Microsoft 365 Mobility and Security | leads4pass | Dec 05, 2022 | MS-101 dumps |
New Question 1:
You need to consider the underlined segment to establish whether it is accurate.
Your company\’s Microsoft 365 subscription includes a Microsoft Azure Active Directory (Azure AD) tenant. to make sure that a tenant user has the ability to publish retention labels from the Security and Compliance admin center using the
minimum permissions necessary, you should assign the user the Global Administrator role.
Select “No adjustment required” if the underlined segment is accurate. If the underlined segment is inaccurate, select the accurate option.
To which role group should you add User1?
A. No adjustment required.
B. Records Management
C. Reviewer
D. Compliance Data Administrator
Correct Answer: B
References: https://docs.microsoft.com/en-us/office365/securitycompliance/file-plan-manager
New Question 2:
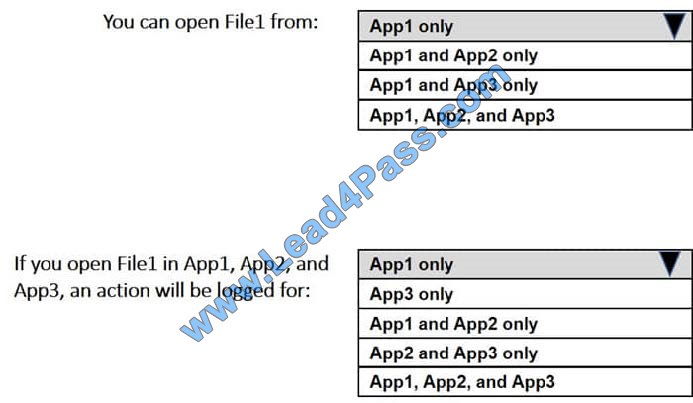
You haw a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
You have three applications named App1, App2, and App3 that have the same file format.
Your company uses Windows Information Protection (W1P) W1P has the following configurations:
Windows Information Protection mode: Silent
Protected apps: App1
Exempt apps: App2
From App1 you create a file named File1.
What is the effect of the configurations? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
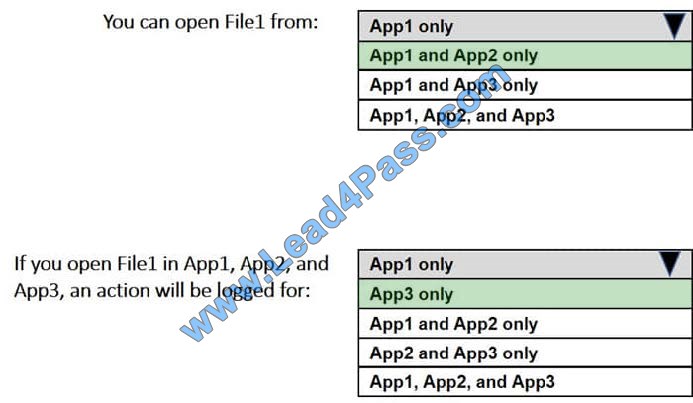
New Question 3:
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a Microsoft Azure Active Directory (Azure AD) tenant.
You have been tasked with assigning a user the minimum required role to allow him to sign up for Microsoft Store for Business.
Solution: You assign the user the Billing account role.
Does the solution meet the goal?
A. Yes
B. No
Correct Answer: B
References: https://docs.microsoft.com/en-us/microsoft-store/roles-and-permissions-microsoft-store-for-business
New Question 4:
You implement Microsoft Azure Advanced Threat Protection (Azure ATP). You have an Azure ATP sensor configured as shown in the following exhibit.

How long after the Azure ATP cloud service is updated will the sensor update?
A. 1 hour
B. 12 hours
C. 48 hours
D. 7 days
E. 72 hours
Correct Answer: E
The exhibit shows that the sensor is configure for Delayed update.
Given the rapid speed of ongoing Azure ATP development and release updates, you may decide to define a subset group of your sensors as a delayed update ring, allowing for a gradual sensor update process.
Azure ATP enables you to choose
how your sensors are updated and set each sensor as a Delayed update candidate.
Sensors not selected for delayed update are updated automatically, each time the Azure ATP service is updated. Sensors set to Delayed update are updated on a delay of 72 hours, following the official release of each service update.
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/sensor-update
New Question 5:
The users at your company use Dropbox Business to store documents. The users access Dropbox Business by using the MyApps portal.
You need to ensure that user access to Dropbox Business is authenticated by using a Microsoft 365 identity. The documents must be protected if the data is downloaded to a device that is not trusted.
What should you do?
A. From the Device Management admin center, configure conditional access settings.
B. From the Azure Active Directory admin center, configure the device settings.
C. From the Azure Active Directory admin center, configure the organizational relationships settings.
D. From the Device Management admin center, configure Exchange on-premises access settings.
Correct Answer: C
New Question 6:
You have a Microsoft 365 E5 subscription.
You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days.
What should you do?
A. From the Cloud App Security admin center, select Users and accounts.
B. From the Microsoft 365 security center, view the Threat tracker.
C. From the Microsoft 365 admin center, view the Security and compliance report.
D. From the Azure Active Directory admin center, view the Risky sign-ins report.
Correct Answer: A
New Question 7:
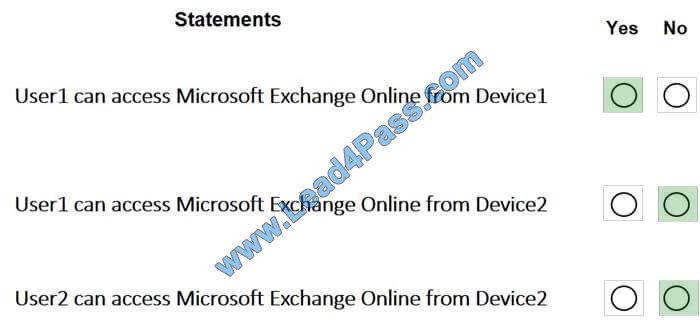
You have the Microsoft Azure Active Director (Azure AD) users shown in the following table.
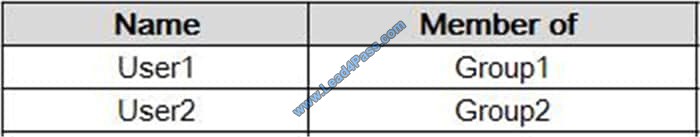
You company uses Microsoft Intune.
Several devices are enrolled in Intune as shown in the following table.

The device compliance policies in Intune are configured as shown in the following table.

You create a conditional access policy that has the following settings:
The Assignments settings are configured as follows:
Users and groups: Group1
Cloud apps: Microsoft Office 365 Exchange Online
Conditions: Include All device state, exclude Device marked as compliant
Access controls is set to Block access.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
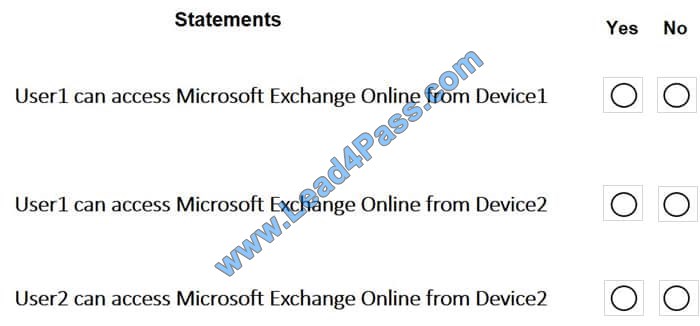
Correct Answer:
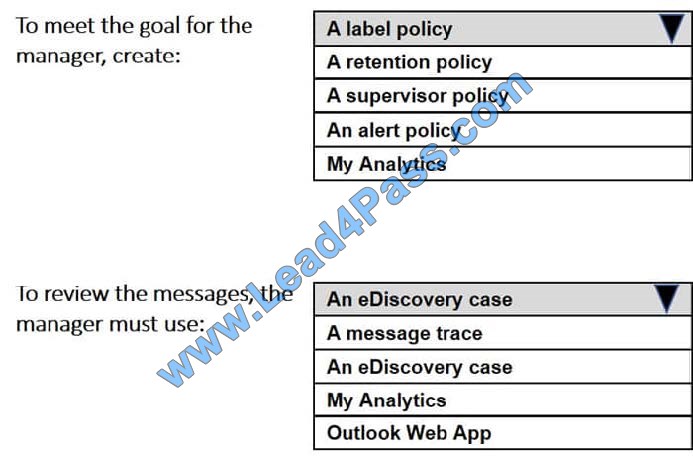
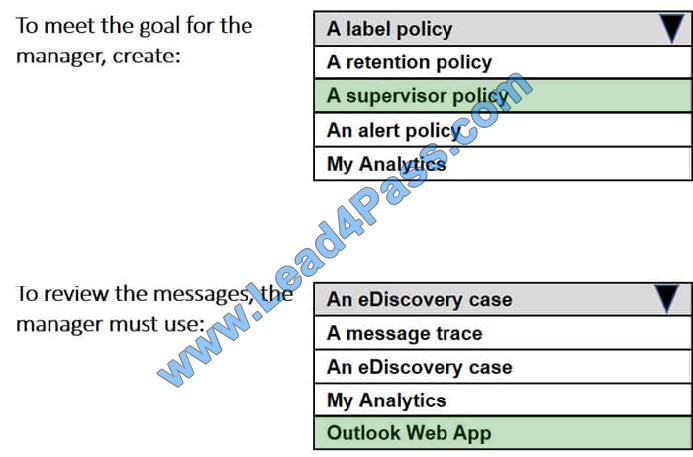
New Question 8:
You have a Microsoft 365 subscription.
You have a group named Support. Users in the Support group frequently send email messages to external users.
The manager of the Support group wants to randomly review messages that contain attachments.
You need to provide the manager with the ability to review messages that contain attachments sent from the Support group users to external users. The manager must have access to only 10 percent of the messages.
What should you do? To answer, select the appropriate options in the answer area.
Hot Area:
Correct Answer:
New Question 9:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Office 365 Advanced Threat Protection (ATP) settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Microsoft 365 admin center, you assign SecAdmin1 the SharePoint admin role.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
You need to assign the Security Administrator role.
New Question 10:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
From Microsoft Defender ATP, you turn on the Allow or block file advanced feature.
You need to block users from downloading a file named File1.exe.
What should you use?
A. a suppression rule
B. an indicator
C. a device configuration profile
Correct Answer: B
New Question 11:
You have a Microsoft 365 subscription.
You need to identify which administrative users performed eDiscovery searches during the past week.
What should you do from the Security and Compliance admin center?
A. Perform a content search
B. Create a supervision policy
C. Create an eDiscovery case
D. Perform an audit log search
Correct Answer: D
New Question 12:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table.

You enroll all the computers in Upgrade Readiness.
You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade.
Solution: You set the ReadyForWindows status of App2 to Highly adopted.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
App1 has a “low install count” (2% or less) so will be Ready to upgrade. We just need to change the setting for App2.
References: https://docs.microsoft.com/en-us/windows/deployment/upgrade/upgrade-readiness-identify-apps
New Question 13:
Note: The question is included in a number of questions that depicts the identical set-up. However, every question has a distinctive result. Establish if the solution satisfies the requirements.
Your company has a Microsoft Azure Active Directory (Azure AD) tenant.
You have been tasked with assigning a user the minimum required role to allow him to sign up for Microsoft Store for Business.
Solution: You assign the user the Purchasing role.
Does the solution meet the goal?
A. Yes
B. No
Correct Answer: B
References: https://docs.microsoft.com/en-us/microsoft-store/roles-and-permissions-microsoft-store-for-business
New Question 14:
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profile?
A. Android
B. CentOS Linux
C. iOS
D. Window 10
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-configure
New Question 15:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table.

You enroll all the computers in Upgrade Readiness.
You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade.
Solution: You set the importance status of App2 to Low install count.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
If an app is installed on less than 2% of the targeted devices, it\’s marked Low install count. Two percent is the default value. You can adjust the threshold in the readiness settings from 0% to 10%. Desktop Analytics automatically marks these apps as Ready to upgrade.
Reference: https://docs.microsoft.com/en-us/configmgr/desktop-analytics/about-deployment-plans
…
Microsoft MS-101 exam questions and answers have been updated and corrected.
Get the complete Microsoft MS-101 dumps https://www.leads4pass.com/ms-101.html (PDF +VCE) 100% pass Microsoft 365 Mobility and Security certification exam.