leads4pass has updated Cisco 350-401 dumps issues! The latest 350-401 exam questions can help you pass the exam!
All questions are corrected to ensure authenticity and effectiveness! Download the leads4pass 350-401 VCE dumps or PDF dumps: https://www.leads4pass.com/350-401.html (Total Questions: 525 Q&A 350-401 Dumps)
Cisco 350-401 Practice testing questions from Youtbe
Latest Cisco 350-401 google drive
[PDF] Free Cisco 350-401 pdf dumps download from Google Drive: https://drive.google.com/file/d/1W1RXS9APDgVZ-8YnYXYhS_4RM-dpb4HM/
Get more complete Cisco CCNP exam certification practice questions https://www.vcecert.com/cisco-dumps/
The latest update of Cisco 350-401 exam questions and answers and official exam information tips
QUESTION 1
Which two operations are valid for RESTCONF? (Choose two.)
A. HEAD
B. REMOVE
C. PULL
D. PATCH
E. ADD
F. PUSH
Correct Answer: AD
Reference: https://www.cisco.com/c/en/us/td/docs/iosxml/ios/prog/configuration/166/b_166_programmability_cg/b_166_programmability_cg_chapter_01011.html
QUESTION 2
What is the function of a control-plane node in a Cisco SD-Access solution?
A. to run a mapping system that manages endpoint to network device relationships
B. to implement policies and communicate with networks outside the fabric
C. to connect external Layer 3 networks to the SD-Access fabric.
D. to connect APs and wireless endpoints to the SD-Access fabric
Correct Answer: A
QUESTION 3
An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button
under the Layer 3 Security options for Web Policy. Which device presents the web authentication for the WLAN?
A. ISE server
B. local WLC
C. RADIUS server
D. anchor WLC
Correct Answer: B
QUESTION 4
How are the Cisco Express Forwarding table and the FIB related to each other?
A. Cisco Express Forwarding uses a FIB to make IP destination prefix-based switching decisions correct
B. The FIB is used to populate the Cisco Express Forwarding table
C. There can be only one FIB but multiple Cisco Express Forwarding tables on IOS devices
D. The Cisco Express Forwarding table allows route lookups to be forwarded to the route processor for processing
before they are sent to the FIB
Correct Answer: A
The Forwarding Information Base (FIB) table?CEF uses a FIB to make IP destination prefix-based switching decisions.
The FIB is conceptually similar to a routing table or information base. It maintains a mirror image of the forwarding
information contained in the IP routing table. When routing or topology changes occur in the network, the IP routing
table is updated, and these changes are reflected in the FIB. The FIB maintains next-hop address information based on
the information in the IP routing table. Reference: https://www.cisco.com/c/en/us/support/docs/routers/12000-seriesrouters/47321-ciscoef.html
QUESTION 5
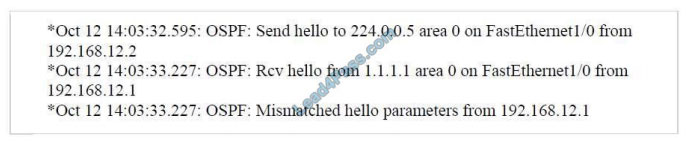
Refer to the exhibit.

Which statement about the OPSF debug output is true?
A. The output displays all OSPF messages which router R1 has sent to received on interface Fa0/1.
B. The output displays all OSPF messages which router R1 has sent or received on all interfaces.
C. The output displays OSPF hello messages which router R1 has sent received on interface Fa0/1.
D. The output displays OSPF hello and LSACK messages which router R1 has sent or received.
Correct Answer: C
This combination of commands is known as “Conditional debug” and will filter the debug output based on your
conditions. Each condition added, will behave like an `And\\’ operator in Boolean logic. Some examples of the “debug IP OSPF hello” are shown below:
QUESTION 6
Which standard access control entry permits from odd-numbered hosts in the 10.0.0.0/24 subnet?
A. Permit 10.0.0.0.0.0.0.1
B. Permit 10.0.0.1.0.0.0.0
C. Permit 10.0.0.1.0.0.0.254
D. Permit 10.0.0.0.255.255.255.254
Correct Answer: C
Remember, for the wildcard mask, 1s are I DON\\’T CARE, and 0s are I CARE. So now let\\’s analyze a simple ACL:
access-list 1 permit 172.23.16.0 0.0.15.255
Two first octets are all 0\\’s meaning that we care about the network 172.23.x.x. The third octet of the wildcard mask, 15
(0000 1111 in binary), means that we care about the first 4 bits but don\\’t care about the last 4 bits so we allow the third octet in
the form of 0001xxxx (minimum:00010000 = 16; maximum: 0001111 = 31).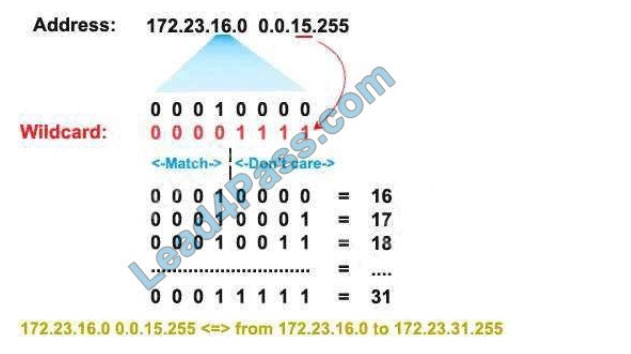
The fourth octet is 255 (all 1 bits) which means I don\\’t care. Therefore network 172.23.16.0 0.0.15.255 ranges from
172.23.16.0 to 172.23.31.255. Now let\\’s consider the wildcard mask of 0.0.0.254 (four-octet: 254 = 1111 1110) which
means we
only care the last bit. Therefore if the last bit of the IP address is a “1” (0000 0001) then only odd numbers are allowed.
If the last bit of the IP address is a “0” (0000 0000) then only even numbers are allowed.
Note: In binary, odd numbers always end with a “1” while even numbers always end with a “0”.
Therefore in this question, only the statement “permit 10.0.0.1 0.0.0.254” will allow all odd-numbered
hosts in the 10.0.0.0/24 subnet.
QUESTION 7
Refer to the exhibit.

During deployment, a network engineer notices that voice traffic is not being tagged correctly as it traverses the
network. Which COS to DSCP map must be modified to ensure that voice traffic is treated properly?
A. COS of 5 to DSCP 46
B. COS of 7 to DSCP 48
C. COS of 6 to DSCP 46
D. COS of 3 to DSCP of 26
Correct Answer: A
QUESTION 8
A company plans to implement intent-based networking in its campus infrastructure.
Which design facilitates migration from a traditional campus design to a programmable fabric design?
A. Layer 2 access
B. three-tier
C. two-tier
D. routed access
Correct Answer: C
Intent-based networking (IBN) transforms a hardware-centric, manual network into a controller-led network that
captures business intent and translates it into policies that can be automated and applied consistently across the
network. The goal is for the network to continuously monitor and adjust network performance to help assure desired
business outcomes. IBN builds on software-defined networking (SDN). SDN usually uses spine-leaf architecture, which
is typically deployed as two layers: spines (such as an aggregation layer), and leaves (such as an access layer).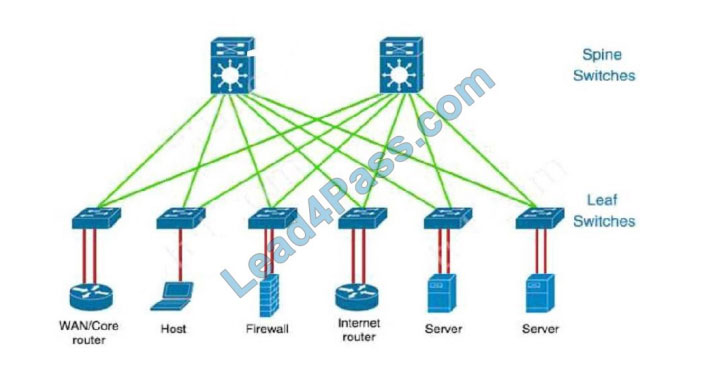
QUESTION 9
An engineer is describing QoS to a client. Which two facts apply to traffic policing? (Choose two.)
A. Policing adapts to network congestion by queuing excess traffic
B. Policing should be performed as close to the destination as possible
C. Policing drops traffic that exceeds the defined rate
D. Policing typically delays the traffic, rather than drops it
E. Policing should be performed as close to the source as possible
Correct Answer: CE
Traffic policing propagates bursts. When the traffic rate reaches the configured maximum rate (or committed information
rate), excess traffic is dropped (or remarked). The result is an output rate that appears as a saw-tooth with crests and
troughs.
Unlike traffic shaping, traffic policing does not cause delay. Classification (which includes traffic policing, traffic shaping, and queuing techniques) should take place at the network edge. It is recommended that classification occur as close to the source of the traffic as possible. Also according to this Cisco link, “policing traffic as close to the source as
possible”.
QUESTION 10
To increase total throughput and redundancy on the links between the wireless controller and switch, the customer
enabled LAG on the wireless controller. Which EtherChannel mode must be configured on the switch to allow the WLC
to connect?
A. Auto
B. Active
C. On
D. Passive
Correct Answer: C
Reference: https://community.cisco.com/t5/wireless-mobility-documents/lag-link-aggregation/ta-p/3128669
QUESTION 11
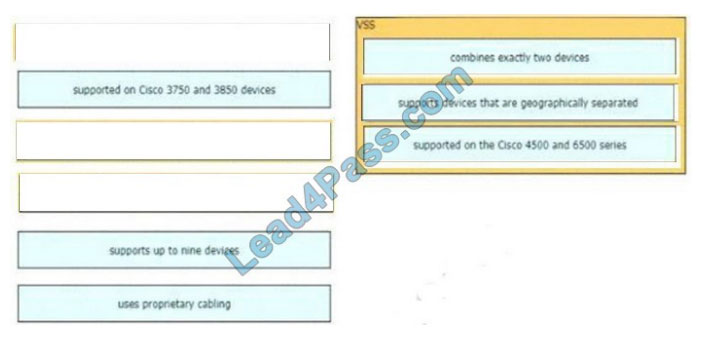
Drag and drop the descriptions of the VSS technology from the left to the right. Not all options are used.
Select and Place:
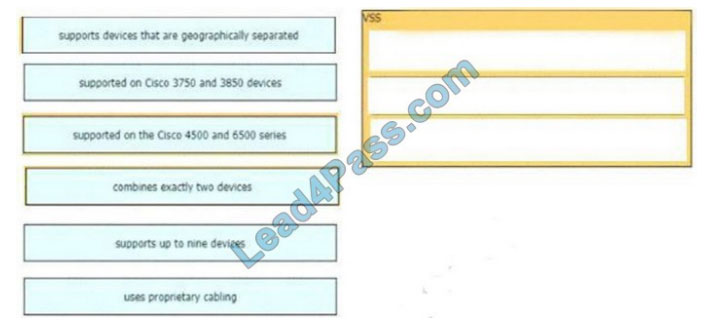
Correct Answer:
QUESTION 12
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A. LISP
B. IS-IS
C. Cisco TrustSec
D. VXLAN
Correct Answer: D
The tunneling technology used for the fabric data plane is based on Virtual Extensible LAN (VXLAN). VXLAN
encapsulation is UDP-based, meaning that it can be forwarded by any IP-based network (legacy or third party) and
creates the overlay network for the SD-Access fabric. Although LISP is the control plane for the SD-Access fabric, it
does not use LISP data encapsulation for the data plane; instead, it uses VXLAN encapsulation because it is capable of
encapsulating the original Ethernet header to perform MAC-in-IP encapsulation, while LISP does not. Using VXLAN
allows the SD-Access fabric to support Layer 2 and Layer 3 virtual topologies (overlays) and the ability to operate over
any IP-based network with built-in network segmentation (VRF instance/VN) and built-in group-based policy. Reference:
CCNP and CCIE Enterprise Core ENCOR 350-401 Official Cert Guide
QUESTION 13
Which NGFW mode block flows crossing the firewall?
A. Passive
B. Tap
C. Inline tap
D. Inline
Correct Answer: D
Firepower Threat Defense (FTD) provides six interface modes which are: Routed, Switched, Inline Pair, Inline Pair with
Tap, Passive, Passive (ERSPAN). When Inline Pair Mode is in use, packets can be blocked since they are processed
inline When you use Inline Pair mode, the packet goes mainly through the FTD Snort engine When Tap Mode is
enabled, a copy of the packet is inspected and dropped internally while the actual traffic goes through FTD unmodified
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/200924-configuringfirepower-threat-defenseint.html
Summarize:
This blog shares the latest Cisco 350-401 exam dumps, 350-401 exam questions and answers! 350-401 pdf, 350-401 exam video! You can also practice the test online! leads4pass is the industry leader!
Select https://www.leads4pass.com/350-401.html leads4pass 350-401 exams Pass Cisco 350-401 exams “Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)”. Help you successfully pass the 350-401 exam.
[Q1-Q13 PDF] Free Cisco 350-401 pdf dumps download from Google Drive: https://drive.google.com/file/d/1W1RXS9APDgVZ-8YnYXYhS_4RM-dpb4HM/